Conditional Just-In-Time Privileged Access Management for your critical resources
Enterprise-Ready • Self-Hosted • Source-Available
Approve, monitor, and expire privileged access automatically — without adding another black-box SaaS. 100% self-hosted, open, and under your control.
Access fast. Stay secure.
GatePlane automates the rest.
Organizations spend countless man/hours, manually providing and removing user access to critical systems, with low or no transparency. GatePlane sits on top of HashiCorp Vault / OpenBao, turning them into full Just-In-Time Access Management system.

The Norm
- Scattered secrets across systems
- Manual approvals via email/messaging
- Shared password without expiration
- No audit trail or compliance tracking*

- Centralized secrets management
- Manual approval workflows remain
- Pre-configured expiration generated passwords
- Logging of who accessed what, and when
Don’t have Vault/OpenBao yet?
We’ll help you install and configure it

With GatePlane
- Conditional, just-in-time access granted only with clear justification
- Centralized, auditable request-approve-expire flow
- Dynamic, time-bound access Automatically approved & revoked
- Full audit trail logging of requests, approvers, and usage metrics
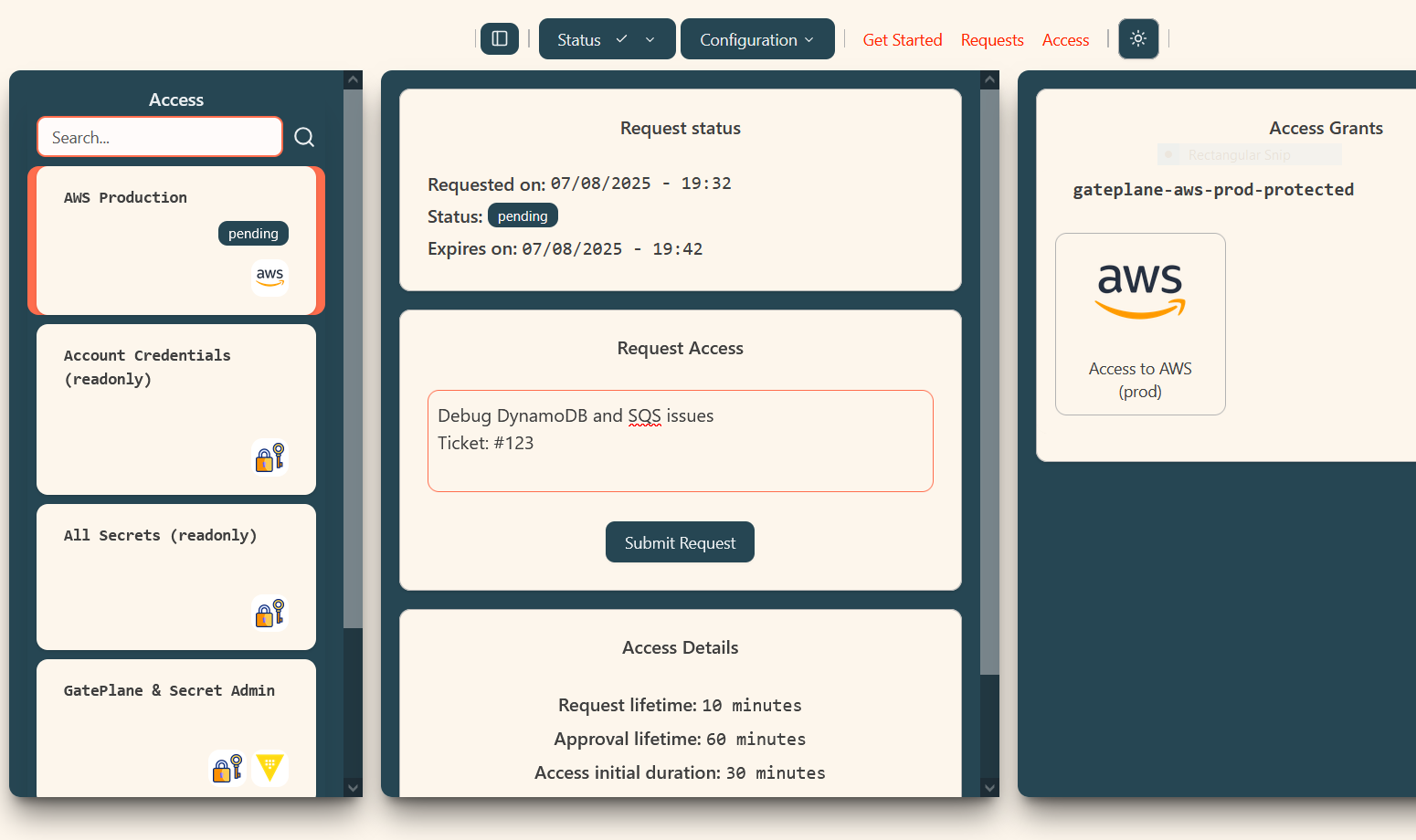
How GatePlane works
Request Access
+ Justification + Duration
Request temporary access to anything: from Databases and Kubernetes (via Vault Policy Gate plugin) to Salesforce and Zendesk (via Okta Group Gate plugin). Directly through the UI Web Interface or CLI.
Approve
1 or more approvers
Approvers review and grant access from the GatePlane dashboard, Slack, Teams, or any CLI. Every approval is logged, timestamped, and fully auditable.
Auto-Expire
Revoke at any time
Credentials are automatically revoked after their approved duration or on demand. Access remains temporary and least-privilege by default.
🪶 No standing privileges. No forgotten keys. Just clear, time-bound access.
Key Features
Intuitive UI Web Interface
Centralizes operations through an intuitive WebUI (hosted at app.gateplane.io), where users can manage access requests, approvals, and claims in a self-service manner.
Just-In-Time Access with TTLs
Grant temporary access only when needed, and let it automatically expire.
GatePlane enforces least-privilege by default through configurable time-to-live (TTL) policies, so credentials exist only for as long as required — no standing privileges, no forgotten keys.
Integration support of 150+ services
Built as a series of plugins that extend Vault or OpenBao.
GatePlane integrates natively with existing secrets engines — AWS, Kubernetes, SSH, databases, and more — as well as existing Okta Integrations — adding conditional, auditable, and approval-based access workflows on top of your trusted foundation.
Self-Hosted & Air-Gapped
Deploy entirely within your own environment — no external dependencies.
GatePlane never interacts with your infrastructure, making it suitable for highly regulated and air-gapped setups where compliance, isolation, and control are essential.
Team Edition
Notification Support Across Messaging Platforms
Notification Support Across Messaging Platforms
Stay informed in real time when access is requested, approved, or claimed.
GatePlane connects with Slack, Microsoft Teams, Discord, or any compatible webhook channel, keeping your team aware of every critical event as it happens.
Team Edition
Access Metrics & Analytics
Access Metrics & Analytics
Track how access is used across your organization.
View metrics like number of requests, mean time to claim, and privilege expiration rates to identify bottlenecks, improve workflows, and maintain a strong security posture.
Enterprise Edition
Dedicated Domain
Dedicated Domain
Get your own branded instance under a custom domain (e.g. myorg.app.gateplane.io).
Each team member signs in through a dedicated, isolated WebUI environment — ensuring stronger identity separation, smoother onboarding, and full control over your organization’s access workflows.
A must have for every role in your team
For DevOps & Platform Engineers
Automate access and stay compliant — without reinventing Vault policies. CLI or WebUI, your choice.
For Security Officers
Gain full audit trails, metrics, and least-privilege by design. No permanent keys. No guesswork.
For Engineering Managers & CTOs
A lightweight, self-hosted alternative to costly PAM suites. Predictable pricing, transparent code, zero lock-in.
For Developers & SREs
Request access in seconds. Get credentials that expire automatically. Less waiting, fewer tickets.
Why GatePlane
Zero Trust by Design
Conditional Okta Group Management
Source Available
Notifications System
Identity Integrations
Conditional Policies

Built on Vault/OpenBao
As a series of plugins
Uses battle-tested, Open-Source software that come with security guarantees out-of-the-box

Self-Hosted & Air-Gapped Ready
For secure deployments
Your infrastructure never interacts with our systems — designed for highly regulated, secure setups.

Source Code Transparency
Source available in full
Inspect, modify, and deploy the core functionality freely. No black-boxes & hidden code.

Simple for Everyone
From novice to expert
Operate through the GatePlane WebUI or automate using Vault and Bao CLI clients.
Simple, Scalable Pricing
Free by default. Add features, like notifications, dedicated domain and support as your team grows
Source Available
All Vault/OpenBao plugins + GatePlane WebUI
- All Vault / OpenBao plugins
- GatePlane UI Web interface access
- Community support
- Self-hosted deployment
🔗 Source Available under Elastic v2
Most Popular
/ per user / month
Integrate with GatePlane Services for Notifications and Insights
- Everything in Community +
- Slack / MSTeams integrations
- Analytics & Metrics
- Human Technical Support
- Priority bug fixes
Dedicated subdomain (myorg.app.gateplane.io) & pre-configured instances
- Everything in Team +
- Dedicated subdomain
- Pre-configured instances
- Custom browser integrations
- Dedicated support channel
- Guided Vault/OpenBao deployment
You have a special case? Let’s Talk
Inside the Cockpit
We’re security engineers who got tired of PAM products that hide behind buzzwords. GatePlane was built because we wanted a transparent, self-hosted alternative — one we’d actually trust in production.

John Torakis
Tech Lead
Experienced security engineer leading the development of the GatePlane platform with a focus on trust, reliability, and open architecture.

Sotiria Giannitsari
Product Lead
Builds and connects the GatePlane community, bridging communication between users and product. Experienced in community management within the security industry.

Kiriakos Sidiropoulos
Operations Lead
Oversees the team’s daily operations and coordination, ensuring smooth collaboration and effective execution across all projects.
Ready to take control of your priviliged access?
Frequently Asked Questions
GatePlane is an on-premise first solution.
We believe that security-critical infrastructure has to be at least under a Source-Available License and deployable on-premise. That said, a cloud solution will follow.
Absolutely!
If you want to give something back, you can always do that in the form of feature requests, community support and even code contributions!
GatePlane was designed to make Privileged Access Management (PAM) a reachable security feature for all organizations.
No!
GatePlane Services (available in Team and Enterprise tiers) are only accessed by browsers (through the GatePlane WebUI), and only to provide notifications and metrics.
GatePlane Services are designed to NEVER access any of the client infrastructure, and no network connectivity between them is needed.
In case your service is in the Secrets Engines supported by Vault / OpenBao, then integration is supported directly through the GatePlane Policy Gate plugin.
Yes! By opening an Github Issue in gateplane-io/vault-plugins repository, you can discuss on an implementation of the feature, and submit Pull Requests,
as GatePlane is powered by the Community.
If you need to support a custom use case, contact us to work out a dedicated solution!
GatePlane Services downtime only affects notifications and metrics provided.
In the case of GatePlane WebUI downtime, all flows can still be used by the CLI tools vault and bao.
You will NEVER lose access to your systems if GatePlane Services go down.
Yes. Always. No chatbots or automated emails.
No. GatePlane works with Vault Community and also supports OpenBao which is open-source and free to use.
Still have questions? Contact us